Information Security Sustainability
Basic Concept
The information assets of any company are a constant security risk, with exposure potentially impacting many stakeholders. Recognizing that ensuring information security is an important social responsibility of companies, GOLDWIN formulated and implemented its Basic Policy on Information Security in March 2008. In view of current trends such as accelerating globalization of business and expansion of e-commerce channels, we revised this policy in October 2021 and developed a management framework that is more in tune with these changes. Our aim is to increase awareness of these diverse risks among all officers and employees, to maintain and improve information security, and to become a more trusted company in society.
Basic Policy on Information Security
Recognizing that ensuring information security is an important issue in the delivery of accurate and efficient business operations, GOLDWIN formulated and implemented this Basic Policy on Information Security with the aim of protecting the company’s information assets.
- Establishment of an information security framework
- To maintain and improve information security, we will secure the required resources and establish a promotional framework for information security activities.
- Protection of information assets
- We will appropriately manage information assets to ensure confidentiality, integrity, and availability, and strive to protect our information assets from all these related threats.
- Compliance with laws and regulations
- We will comply with laws and regulations related to information security.
- Education and training
- We will provide regular education and training to ensure our officers and employees are sufficiently aware of their responsibilities and obligations to ensure information security.
- Continuous improvement
- To respond to changes in risk associated with revisions to laws and regulations related to information security, and technical innovations, we will regularly evaluate and revise this Basic Policy on Information Security, our other related policies, and management systems, as we strive to continually improve our information security.
- Incident handling
- We will work to prevent incidents related to information security and, in the event that an incident occurs, we will not only respond to the incident but also take prompt and appropriate measures, including measures to prevent recurrence.
Established: March 17, 2008
Revised: October 1, 2021
Promotion Framework and Person Responsible
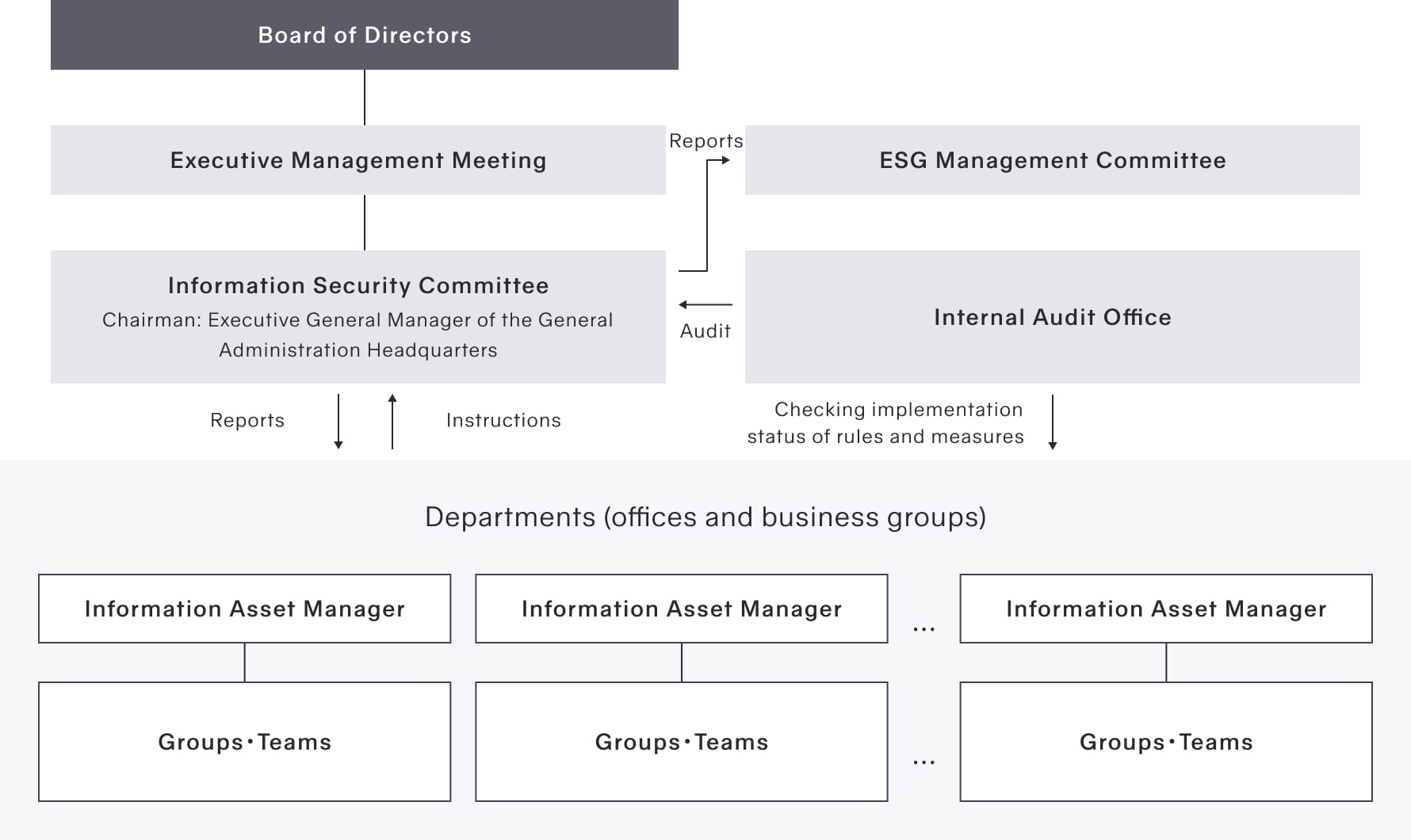
GOLDWIN operates an information security promotion framework with the Information Security Committee, which was established in October 2021, having responsibility. The Information Security Committee is chaired by the Executive General Manager of the General Administration Headquarters, who oversees the Information Systems Division, with oversight and guidance on important matters received from the Board of Directors through the Executive Management Meeting. The committee meets twice a year as a rule, but the chairman may convene a meeting at any time if necessary.
The General Manager of each department, office, or business group is in charge of managing information assets and works as liaison between the division and the Information Security Committee. The General Manager is in charge of communicating instructions from the Information Security Committee to the employees, and implementing those instructions.
Information Security Education
With human error being the cause of many security incidents, including information leaks, improving the information security awareness and literacy of every employees is essential for preventing incidents from occurring.
In FY 2022, we conducted a series of e-learning and group training programs to educate employees on a range of related matters, including our approach to information security, case studies of incidents and related measures, as well as internal systems and rules. All 1,494 applicable employees (office workers) participated in the programs. As for sales staff, training materials are sent to each store and training is provided by each store manager. All 244 relevant stores have completed the training.
We will revise the content of our curriculum as needed and update details in light of the current state of rapidly changing information technology.
Training for Targeted Email Attacks
In FY 2022, we conducted two drills for targeted email attacks to raise employee perception of cyberattacks as being a risk that can affect them.
In recent years, there has been a spate of cases in which important information has been stolen or ransom money demanded from specific companies and organizations through targeted email attacks, as well as cases in which money has been extracted through scam business emails. We have also received similar emails. As a measure to combat this, the Information Security Committee Administrative Office sent a mock email attack to employees as a training exercise. By actually exposing employees to targeted email attacks, they will learn not to open suspicious emails, not to click on URLs in the body of suspicious emails, and not to open attachments, thereby reducing the risk of virus infection, information leaks, and other problems. Employees who opened the attached files during both drills are required to retake the e-learning course and undertake other education.
Commitment to Information Asset Management
To strengthen companywide management of information assets under this new framework, it is important that we restructure our management rules. In FY 2021, we began working to understand the situation with internal management of information assets as the first step toward achieving this goal. After asking each division about which information assets they hold and how they are currently managing them, we have been analyzing the status of operations.
Under the GOLDWIN document handling rules, we have defined three standards: Strictly Confidential, Confidential, and For Internal Use Only. In FY 2021, we conducted a survey of personal information and other information classified as Strictly Confidential, which requires the highest level of control, and in FY 2022, we conducted an inventory of information assets by expanding the scope to include Group companies. Going forward, we will clearly identify our information assets to ensure documentation, companywide uniformity, and compliance with the management rules.
Furthermore, in addition to our commitment to information asset management, we are also working to strengthen restrictions on the use of USB memory devices. We clarified the criteria for approved use, and we reexamined devices that have already been approved. In FY 2023 onward, restrictions on USB use will be further strengthened, including limiting PCs to which USB memory devices can be connected.
Information Security Incident Support Center
When information security incidents occur, it is extremely important to receive a prompt report from the relevant person, and to respond as an organization. In August 2021, we established and began operating a new Information Security Incident Support Center in preparation for such a situation. In FY 2022, there were 25 inquiries, of which 21 were about spam emails. We are also explaining to all employees that if they find an incident potentially leading to an information leak, they must report it to their division superior and contact the support center immediately.
Examples of information security incidents
- Losing a computer or other information device
- Opening an attached file or accessing a URL in an unsolicited or spam email
- Installing a file infected with a virus
- Having an ID to the company social media, etc. hacked
- Disclosing personal information accidentally
Future Issues
With the importance of information security continuing to increase, we will improve the level of management in terms of technologies, operations, systems, and education going forward. We will also establish appropriate management indicators as we steadily advance our objectives.
From next fiscal year, we plan to assess risks related to the essential computers, networks, and other devices we use for business, and to investigate priority measures. In addition, we plan to further strengthen our systems by securing specialists in information security management and establishing a dedicated organization.
